 If this story motivates you take action immediately, then this post was worth writing. I’ll explain why it is so critical (and easy, frankly) to backup, secure and ensure that your laptop, smartphone or tablet devices are locked down so you are protected. I’ll also tell you why it is easier than ever—and critical to police recovery efforts—to make certain your devices are able to be tracked.
If this story motivates you take action immediately, then this post was worth writing. I’ll explain why it is so critical (and easy, frankly) to backup, secure and ensure that your laptop, smartphone or tablet devices are locked down so you are protected. I’ll also tell you why it is easier than ever—and critical to police recovery efforts—to make certain your devices are able to be tracked.
Last Wednesday evening my daughter was in a good area of St. Paul, parked on a busy street, and hanging out with friends in a popular cafe nearby. Coming out to her car around 10:30pm, she discovered her driver side rear window was smashed in and her backpack—containing her 11″ Macbook Air, iPod nano, two of her college textbooks, her medications and much more—had been stolen.
Ironically, two St. Paul police officers were eating in that same cafe so she immediately filed a report. With thousands of these sorts of thefts each year, it’s probably understandable that TWO DAYS went by with no contact and zero action on the part of the St. Paul Police Department, even after my daughter called numerous times.
But because my daughter smartly installed tracking software on her Macbook Air, as soon as the suspected thief got online with her laptop it began “phoning home” EVERY 8 MINUTES.
As a consequence, we had webcam photos of the suspect, screenshots of his activities (e.g., Facebook, Wells Fargo banking, and his general surfing) along with a log of the dynamically issued IP address of his DSL connection.
After she told me Friday afternoon (after her third inquiry to St. Paul Police) that she’d been informed that, “…an investigator hasn’t been assigned to the case yet so why don’t you call back on Monday“, I became very upset. As such I started working on this issue when my workday was done on Friday about 4:30pm which, unbeknownst to me, would consume the next five hours and several additional hours the next day.
The results were amazing, disconcerting, but ultimately fulfilling.
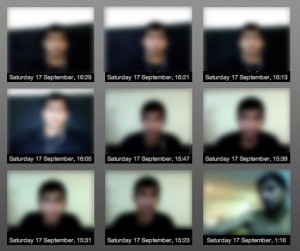
Intentionally blurred photos of the suspected thief from the tracking software webcam results
Imagine you had placed tracking software on your computer and it was phoning home with webcam photos, screenshots and an internet protocol (IP) address and that you KNOW it is trivial to track the suspected thief down.
Coupled with that would be knowing that—if the St. Paul police would simply respond and CALL—they could be handed all of this data on a silver platter and have immediate probable cause to take action.
Then they could easily create a subpoena to require the suspect’s ISP to provide the physical location that matches that IP address, get a search warrant, and go arrest him and retrieve my daughter’s laptop.
As you may or may not know, internet service providers are compelled to answer a subpoena of this type which is a legal request (i.e., signed by a judge) to provide the physical location address to which that dynamic IP address was assigned at that moment.
There is no question that St. Paul police have bigger-fish-to-fry and, as one officer told me, “we have thousands of these sorts of cases per year.” My position with the mayor and with the police officers was that having this sort of pinpointed data was just like driving by a restaurant parking lot two days after a car was stolen and seeing it parked there, and the police being unwilling to send a squad car over in order to see who climbs in it, then arrest them and get the car back to its rightful owner.
THE UNFOLDING
In any event, I can’t say too much more at this point since my daughter’s case is an ongoing investigation, but here is what transpired which I think you’ll find interesting:
1. Scouring the screenshots Friday night, I discover the suspect’s name and email address. That leads me to a post on an obscure forum which contained his home address
2. After calling the St. Paul police watch commander to request someone call me so I could give them this data and HELP THEM apprehend the suspect and retrieve the stolen laptop, I get NO RESPONSE. Not knowing what action to take next, I went online to “IP Locator” websites in an attempt to verify the physical location of the suspect’s IP address and see if it matches the physical address I now have
3. Unfortunately I had only lukewarm success discovering a physical location so I reached out to a friend of mine who had owned an ISP in St. Paul to ask if *he* knew of any reliable and accurate IP locator sites. He schooled me on how inaccurate all of these are, especially when it comes to dynamically issued DSL IP addresses. But in an email that followed moments later, he asked if I’d be interested in him pinging a guy he knows, St. Paul mayor Chris Coleman, to elicit his help and he immediately sent off an introductory email to the mayor and I. The mayor then indicated he’d followup on it
4. Now I had to figure out how to communicate all of this data to the mayor and to clearly show him why I was so agitated and to continue to drive ahead on getting the St. Paul police to take action. So I did what any geek might do: I created a password protected webpage and embedded a screencast of the Undercover tracking website showing all of the webcam photos taken of the suspect, screenshots of computer activity, and an IP address access log (which I’d learned was assigned to a location in Minneapolis). The video explained it all, including why I was so frustrated with his department’s inaction since this was a no-brainer to go arrest this guy and get the laptop back. About an hour later I emailed the mayor the URL and password to the page so he could view it.
5. Mayor Coleman emailed back late Friday night that he would take action. But by close to Noon the next morning (Saturday) nothing had happened. So I emailed him again and told him I’d reviewed the suspect’s Facebook chats and it was clear he might sell the Macbook Air…so time was of the essence.
6. Two hours later on Saturday afternoon I receive a call from a St. Paul police sergeant. He takes down all my info, I add to the webpage I’d created for the mayor and include all of the webcam photos, screenshots and the IP log showing the IP address the suspect was coming in on and email him the login information. The sergeant indicates he’s going to obtain an administrative subpoena and take action and he’d call me back later.
7. The sergeant calls about 3pm. He’s going to get the subpoena and search warrant signed and “round up some officers” to go and arrest the suspect and he’d call back with results.
8. He calls about 6:15pm and he tells me they performed a felony arrest and they had my daughter’s Macbook Air! My wife, daughter and I hopped in the car immediately and met the sergeant at the police station in downtown St. Paul and he handed her the computer.
Let me stop for a second and give kudos to Mayor Coleman for motivating the St. Paul police to address our theft immediately and, most importantly, for Sgt. Steve Smith for his amazing work on wrapping this up in one day (though he has much work yet to do no doubt). Smith was incredibly gracious (and apologetic for the department’s previous inaction which was truly appreciated) and was even willing to drive halfway between St. Paul and the western suburbs in order to get us the laptop…but he’d done enough so we came down to the station).
Though everything else that was stolen is still missing (the search of the suspect’s apartment didn’t turn up any of my daughter’s other stolen items), with the suspect facing felony break-in and/or receiving stolen merchandise charges, we hope he will either confess or turn over the perpetrators.
Wow. The tracking software worked amazingly well. We had a full log and photos which provided probable cause for the police to get both the subpoena and the search warrant, and can now be used as evidence.
HOW TO PROTECT YOURSELF
But…and this is a big but…there are some things my daughter should have done to further protect herself and this is what you might do to protect yourself (starting with NOT leaving a backpack with all of your stuff in the car!).
Think about how integrated all of your accounts are today. If a thief steals your device, they likely will instantly have access to your email account. With that they can change passwords on every one of your accounts!
Plus, many of us enable our web browsers to store our passwords within them so we can automatically login. If a thief has access to your web browser with its stored passwords, they could hijack Twitter, Facebook, your banking website (though most banks don’t allow password storage locally) and other accounts like Dropbox and so on.
So what do you do? In case your computer, smartphone or laptop is stolen (below is for Mac users but I point out software below for Windows users):
 a) The tracking software my daughter had on her Macbook Air is called “Undercover Mac“. It runs on Mac OS X Tiger, Leopard, Snow Leopard or Lion. It creates its own partition so, even if a crook sets up a new user account and deletes yours, the software remains and will phone home whenever the computer is online.
a) The tracking software my daughter had on her Macbook Air is called “Undercover Mac“. It runs on Mac OS X Tiger, Leopard, Snow Leopard or Lion. It creates its own partition so, even if a crook sets up a new user account and deletes yours, the software remains and will phone home whenever the computer is online.
That said, a Mac-savvy thief could’ve easily performed a “clean install” of OS X and erased the internal hard drive (or solid state drive (SSD) in the case of the Macbook Air) and along with it Undercover Mac. Since Apple has enabled “firmware password” capability in their computers, if you enter a firmware password a thief cannot do a clean install. Undercover Mac would then remain on the drive and do its job.
b) My daughter should have had “FileVault2” setup on her Macbook Air for her primary admin account. The new Lion-based FileVault is *extremely* secure and has no discernible “overhead” (meaning that, once you log in to your primary user account, you will not notice any slowdown in performance). In this way, she would not have had to worry AT ALL of a thief changing her passwords. As soon as she got home the night her stuff was stolen, she had to log on to all of her accounts and change her passwords to ensure all of her accounts were protected.
Then, in order to lure in the thief and ensure Undercover can do its phoning home job, it’s recommended to create a dummy account that will enable the thief to play around on your Mac. This account should have a blank password and no admin privileges
c) If your laptop is stolen, Undercover has an account site where you can immediately go in and report the device stolen and enter the case number, police department, officer and phone number. That activates Undercover and, the moment the computer gets online regardless whether it’s at the thief’s home or in a coffee shop, it begins sending the data. Then you can login and watch the activity unfold as it loads photo after photo, screenshot after screenshot
d) Undercover also has software for iOS devices (iPhone; iPod; iPad), even though Apple offers a “Find my…” tracking software in their MobileMe offering (and “Find my Mac” has shown up in iCloud, launching soon)
e) Fortunately my daughter owns a 2TB Time Machine Apple Airport which means 100% of her Macbook Air’s SSD was backed up. She’s already re-imaged her MBAir and it is in exactly the same state as it was before it was stolen (and yes, she cleaned the keyboard with alcohol and wiped it down with screen cleaner!).
BUT I USE WINDOWS (OR LINUX OR ANDROID)
 A free alternative that works on Windows, Linux, Mac and Android (with a “Pro” paid option that includes additional features and many more devices) is called “Prey“. As they say on their website, “Prey lets you keep track of your phone or laptop at all times, and will help you find it if it ever gets lost or stolen. It’s lightweight, open source software, and free for anyone to use. And it just works.”
A free alternative that works on Windows, Linux, Mac and Android (with a “Pro” paid option that includes additional features and many more devices) is called “Prey“. As they say on their website, “Prey lets you keep track of your phone or laptop at all times, and will help you find it if it ever gets lost or stolen. It’s lightweight, open source software, and free for anyone to use. And it just works.”
Basically you install a tiny agent in your computer or phone, which silently waits for a remote signal to wake up and work its magic.
This signal is sent either from the Internet or through an SMS message, and allows you to gather information regarding the device’s location, hardware and network status, and optionally trigger specific actions on it.
Prey advantages include:
- It is open source and free version has what most of us need
- You can run it on your own servers (best for you privacy concerned folks who want to be guaranteed the Prey folks can’t see your data)
- The instruction set to your devices can be sent by Prey in an encrypted form
- To stop formatting of your drive, Prey recommends what Undercover does about setting a firmware password: “We encourage you to add a BIOS password and disable booting from removable devices on your PC, so that the thief will be forced to boot into the previous installation and thus, not be able to format your hard disk easily. If you have a Mac, there’s a firmware password utility on your Mac OS installation DVD. You can find it in in Applications/Utilities on the disc.“
Bottom line? You are more vulnerable than ever to having a mobile device stolen, especially since they’re so small and portable now and you have them with you most of the time. Since so many people I know don’t want to be bothered with entering a password on their laptop (so when awakened from sleep mode the computer is ready or smartphone or tablet instantly on), when it is stolen the device is WIDE OPEN for the thief to compromise everything and all of the social media and other offerings you engage in online.
So back up your computer; encrypt your drive and password protect your primary user account; run a tool like Undercover or Prey; use services like MobileMe (now free) and set up “Find my…” on your iPhone or iPad. If you do, it is likely you’ll also have a happy ending to your theft story if it occurs.
VIDEOS
Overview of Undercover Mac
Overview of Prey