Our friend over at Blandin on Broadband, Ann Treacy, had this post about Minnesota ranking #1 in internet usage:
Our friend over at Blandin on Broadband, Ann Treacy, had this post about Minnesota ranking #1 in internet usage:
Entrepreneur Magazine just called out Minnesota as the state with the highest rate of Internet usage…
According to data from the U.S. Department of Commerce’s National Telecommunications and Information Administration, you won’t find the most connected people on the coasts, or deep in the heart of Texas, but largely in the Midwest. Just under three-quarters of U.S. households were online in 2015. But the most connected state isn’t located on one of the coasts — it’s in the heart of the Midwest…
In 2015, 83.1 percent of Minnesotans, or 4,307,850 households, used the internet. In 1998, 1,889,017 (then 41.5 percent) households were online.
It’s great to see Minnesota rank highly! However before we drink too much champagne, there are a couple of caveats – they are talking about Internet usage, not necessarily broadband. And they are talking about use anywhere (library, work, coffee shop, school), not necessarily home. We come in third for home access with 76.2 percent, which is good but still Internet access – not necessarily broadband.
We agree with Ann that it’s good to see Minnesota ranked so highly but our broadband is still lacking state-wide. Read more from Ann and follow Blandin on Broadband.
 On December 13, 2013 the security researcher,
On December 13, 2013 the security researcher,  Most of us know that it is simple to report fraud on a credit card, have your card reissued, and at most we’re at risk for $50 if we report it within 60 days. What most people do NOT know is that using a debit card could cause your bank account to be drained and end up with you needing to fight, potentially for months, to get your money returned in to your account.
Most of us know that it is simple to report fraud on a credit card, have your card reissued, and at most we’re at risk for $50 if we report it within 60 days. What most people do NOT know is that using a debit card could cause your bank account to be drained and end up with you needing to fight, potentially for months, to get your money returned in to your account.
 1) Independent ATMs – You run the risk of skimmers. While skimmers can be found on bank ATMs, they’re less likely because there are often security cameras in place.
1) Independent ATMs – You run the risk of skimmers. While skimmers can be found on bank ATMs, they’re less likely because there are often security cameras in place. 6) Discover your bank’s debit card policies – One would think our bank, Wells Fargo (which is the 4th largest in the U.S.) would clearly spell out their debit card policies and how they protect us, right? Nope. It was startlingly obtuse and caused me to dig around alot…and I still didn’t get all my questions answered.
6) Discover your bank’s debit card policies – One would think our bank, Wells Fargo (which is the 4th largest in the U.S.) would clearly spell out their debit card policies and how they protect us, right? Nope. It was startlingly obtuse and caused me to dig around alot…and I still didn’t get all my questions answered. Here is one last data point for your consideration about whether or not to consider using a debit card as you shop going forward: debit cards carry higher risks for everyone so fees are likely to go up.
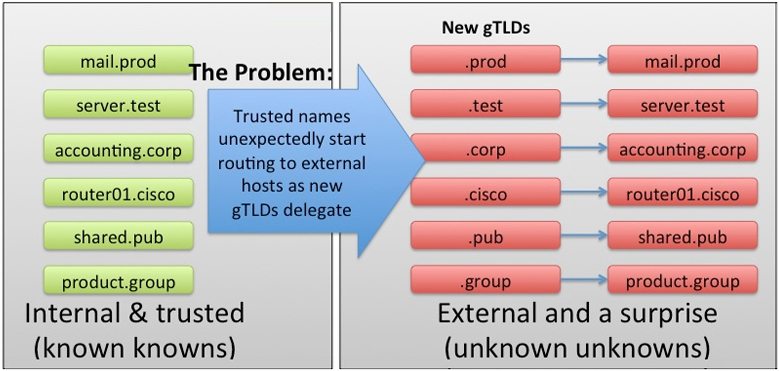
Here is one last data point for your consideration about whether or not to consider using a debit card as you shop going forward: debit cards carry higher risks for everyone so fees are likely to go up. What if the generic Top Level Domains (
What if the generic Top Level Domains (
 One of the reasons healthcare costs have spun out of control is that most consumers are blind to those costs. There isn’t an easy method of shopping for price and little-to-no incentive for doing so since most consumers only care about their small co-pay.
One of the reasons healthcare costs have spun out of control is that most consumers are blind to those costs. There isn’t an easy method of shopping for price and little-to-no incentive for doing so since most consumers only care about their small co-pay.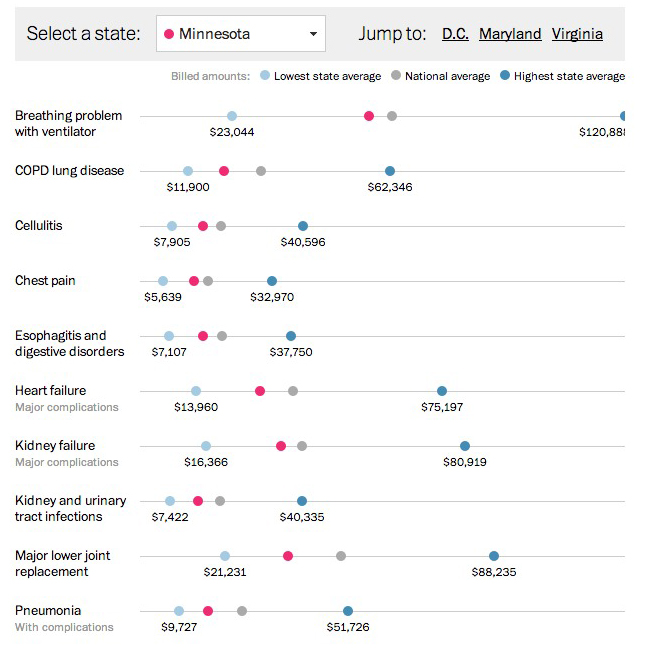


 The University of Minnesota launched an
The University of Minnesota launched an  Here is a followup to the post, “
Here is a followup to the post, “
 Students in grades K-12 will be teaching adults how to use iPads, iPods, and other devices and software programs. Conference highlights include:
Students in grades K-12 will be teaching adults how to use iPads, iPods, and other devices and software programs. Conference highlights include: More than 400 organizations have publicly expressed support of the contentious Stop Online Piracy Act (SOPA), or the passage of other similar anti-piracy legislation, and we were stunned to see that Minnesota-based
More than 400 organizations have publicly expressed support of the contentious Stop Online Piracy Act (SOPA), or the passage of other similar anti-piracy legislation, and we were stunned to see that Minnesota-based